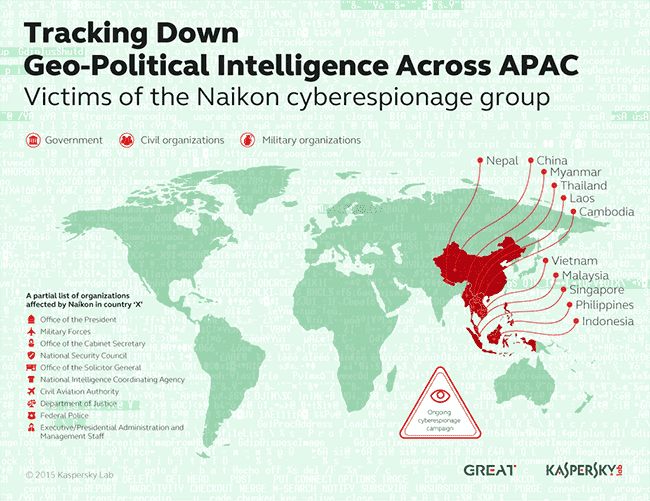
From setting up spying infrastructure within a country’s borders for real-time connections and data mining, to spying tools with 48 commands, a new report by Kaspersky Lab shows how the threat actor Naikon has spent the last five years successfully infiltrating national organisations around the South China Sea.
From setting up spying infrastructure within a country’s borders for real-time connections and data mining, to spying tools with 48 commands, a new report by Kaspersky Lab shows how the threat actor Naikon has spent the last five years successfully infiltrating national organisations around the South China Sea.
Experts have discovered that Naikon attackers appear to be Chinese-speaking and that their primary targets are top-level government agencies and civil and military organizations in countries such as the Philippines, Malaysia, Cambodia, Indonesia, Vietnam, Myanmar, Singapore, Nepal, Thailand, Laos and China.
Kaspersky Lab has identified the following hallmarks of Naikon operations:
- Each target country has a designated human operator, whose job it is to take advantage of cultural aspects of the country, such as a tendency to use personal email accounts for work;
- The placing of infrastructure (a proxy server) within the country’s borders to provide daily support for real-time connections and data exfiltration;
- At least five years of high volume, high profile, geo-political attack activity;
- Platform-independent code, and the ability to intercept the entire network traffic;
- 48 commands in the repertoire of the remote administration utility, including commands for taking a complete inventory, downloading and uploading data, installing add-on modules, or working with the command line.
The Naikon cyberespionage threat actor was first mentioned by Kaspersky Lab in its recent report, “The Chronicles of the Hellsing APT: the Empire Strikes Back” where the actor played a pivotal role in what turned out to be a unique story about payback in the world of advanced persistent threats. Hellsing is another threat actor who decided to take revenge when hit by Naikon.
“The criminals behind the Naikon attacks managed to devise a very flexible infrastructure that can be set up in any target country, with information tunneling from victim systems to the command center. If the attackers then decide to hunt down another target in another country, they could simply set up a new connection. Having dedicated operators focused on their own particular set of targets also makes things easy for the Naikon espionage group,” – says Kurt Baumgartner, Principal Security Researcher, the GreAT team, Kaspersky Lab.
Naikon’s targets are hit using traditional spear-phishing techniques, with emails carrying attachments designed to be of interest to the potential victim. This attachment might look like a Word document, but is in fact an executable file with a double extension.
Kaspersky Lab advises organizations to protect themselves against Naikon as follows:
- Don’t open attachments and links from people you don’t know
- Use an advanced anti-malware solution
- If you are unsure about the attachment, try to open it in a sandbox
- Make sure you have an up-to-date version of your operating system with all patches installed
Kaspersky Lab protects users against the threat, using Automatic Exploit Prevention functionality, strong heuristics and emulation to detect Naikon’s components as: Exploit.MSWord.CVE-2012-0158, Exploit.MSWord.Agent, Backdoor.Win32.MsnMM, Trojan.Win32.Agent and Backdoor.Win32.Agent.
To learn more about the “Naikon” threat actor, please read the blog post at Securelist.com.