Kaspersky Lab spam analysts have found examples of a mass mailing targeting users in the US
Kaspersky Lab spam analysts have found examples of a mass mailing targeting users in the US. In their emails, the spammers refer to the tragic events that have recently hit the headlines, predict a wave of similar disasters still to come and offer readers a simple way to protect themselves and their family if the worst happens. For a few dozen dollars these ‘well-wishers’ will share a video tutorial detailing how to build a miraculous electricity generator in their own homes.
One of the mailings reads: “Blood on streets in France will spread to the U.S.A”. In this email, the spammers paint a bleak picture of America’s immediate future, claiming the government is hiding the truth but expects blood to flow in the streets is “it did in France”. But there is an answer – just click the link and you’ll find out how to protect your family from any attack.
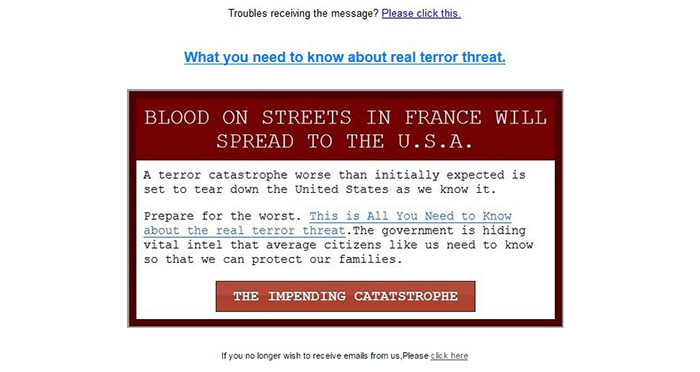
When users follow these links they are taken to sites that are also striking. They start with an audio presentation of a confidential story told by a well-wisher. The narrator mentions a miracle generator so simple to assemble that even your grandmother could do it. Happy buyers don’t only get an autonomous source of energy to be used in the event of disaster; they can also save on household energy bills. This generator promises independence from traditional energy supplies and will allegedly work flawlessly in the face of any terrorist attack or natural disaster.
"Spammers traditionally exploit news stories to play on readers’ sympathies or fears in the hope of earning money. This time the recipient of the mailing had a choice – to pay for the video tutorial, or to ignore the message. But next time the link might hide malicious software that can steal users’ financial data or spy on them. This malware should be handled by an anti-virus solution; paying (or not) for the services of ‘well-wishers’ is completely at the user’s discretion," said Anna Volodina, Lead Spam Analyst at Kaspersky Lab.
The full version of the report is available at Securelist.com.
