Kaspersky Lab’s Global Research and Analysis Team has discovered Blue Termite – a cyberespionage campaign that has been targeting hundreds of organizations in Japan for at least two years
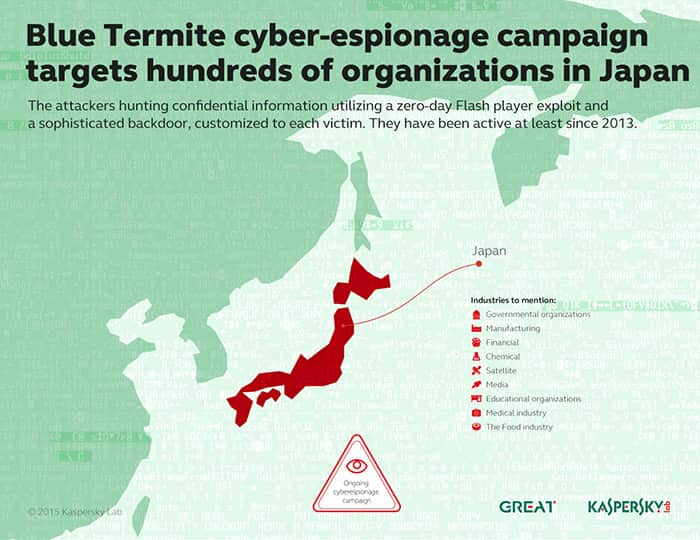
Kaspersky Lab’s Global Research and Analysis Team has discovered Blue Termite – a cyberespionage campaign that has been targeting hundreds of organizations in Japan for at least two years. The attackers hunt for confidential information and utilize a zero-day Flash player exploit and a sophisticated backdoor, which is customized for each victim. This is the first campaign known to Kaspersky Lab that is strictly focused on Japanese targets - and it is still active.
In October 2014 Kaspersky Lab researchers encountered a never before seen malware sample, which stood out from others because of its complexity. Further analysis has shown, that this sample is only a small part of a large and sophisticated cyberespionage campaign.
The list of targeted industries includes governmental organizations, heavy industries, financial, chemical, satellite, media, educational organizations, medical, the food industry and others. According to results of the investigation, the campaign has been active for about two years.
Various infection techniques
To infect their victims, Blue Termite operators utilize several techniques. Before July 2015 they mostly used spear-phishing emails – sending malicious software as an attachment to an email message with content, which would be likely to attract a victim. However in July the operators changed their tactics and have started to spread the malware via a zero-day Flash exploit (CVE-2015-5119, the exploit which was leaked by The Hacking Team incident earlier this summer). The attackers have compromised several Japanese websites so that visitors of the sites would automatically download an exploit once they are on the website and become infected. This is referred to as a drive-by-downloads technique.
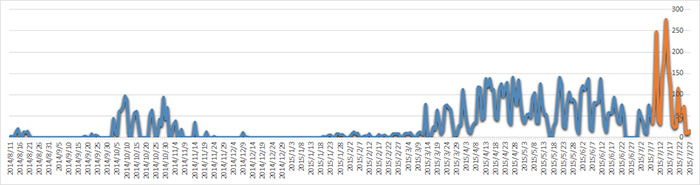
Blue Termite infection rate in 2014-2015
The implementation of a zero-day exploit led to a significant spike in the infection rate registered by Kaspersky Lab detection systems in the middle of July.
There were also attempts to profile the victims registered. One of the compromised websites belonged to a prominent member of Japanese government and another one contained a malicious script that would filter out visitors from all IPs except one belonging to a specific Japanese organization. In other words, only chosen users would get the malicious payload.
Exclusive malware and language artefacts
After a successful infection, a sophisticated backdoor is deployed on a targeted machine. The backdoor is capable of stealing passwords, downloading and executing additional payload, retrieving files etc. One of the most interesting things about the malware used by the Blue Termite actor is that each victim is supplied with a unique malware sample that is made in a way that it could only be launched on a specific PC, targeted by the Blue Termite actor. According to Kaspersky Lab researchers, this has been done in order to make it difficult for security researchers to analyze the malware and detect it.
The question of who is behind this attack remains unanswered. As usual, attribution is a very complicated task when it comes to sophisticated cyberattacks. However, Kaspersky Lab researchers were able to collect some language artefacts. In particular, the graphic user interface of the Command and Control server as well as some technical documents related to the malware used in the Blue Termite operation are written in Chinese. This could mean that actors behind the operation speak this language.
As soon as Kaspersky Lab researchers had gathered enough information to confirm that Blue Termite is a cyberespionage campaign targeting Japanese organizations, company representatives informed local law enforcement agencies about these findings. As the Blue Termite operation is still ongoing, Kaspersky Lab’s investigation is also continuing.
“Although Blue Termite is not the first cyber espionage campaign to target Japan, it is the first campaign known to Kaspersky Lab, to be strictly focused on Japan targets. In Japan it is still a problem. Since early June, when the cyberattack on the Japan Pension Service started to be widely reported, various Japanese organizations would have started to deploy protection measures. However, the attackers from Blue Termite, who might have kept a close eye on them, started to employ new attack methods and successfully expanded their impact,” said Suguru Ishimaru, Junior Researcher at Kaspersky Lab.
In order to reduce the risk of being infected by the Blue Termite cyberespionage campaign Kaspersky Lab experts recommend the following measures:
- Keep software updated, especially software that is widely used and often exploited by cyber criminals;
- If you are aware of any vulnerabilities in the software on your device but there is no patch for it yet, avoid using this software;
- Be suspicious of emails with attachments;
- Use a proven anti-malware solution.
Kaspersky Lab products successfully detect and block the malware with the following detection names:
- Backdoor.Win32.Emdivi.*
- Backdoor.Win64.Agent.*
- Exploit.SWF.Agent.*
- HEUR:Backdoor.Win32.Generic
- HEUR:Exploit.SWF.Agent.gen
- HEUR:Trojan.Win32.Generic
- Trojan-Downloader.Win32.Agent.*
- Trojan-Dropper.Win32.Agent.*
More information about the Blue Termite targeted attacks is available to Kaspersky Security Intelligence Services customers. Contact: intelreports@kaspersky.com
Learn more about Blue Termite cyber espionage campaign on Securelist.com
Learn how Kaspersky Lab products can help protect against the Blue Termite operation here: https://business.kaspersky.com/bluetermite-apt/4409
Learn more about other cyber espionage operations that target or have targeted Japan previously here: https://apt.securelist.com/#secondPage/countriesdata=39
Learn how sophisticated targeted attacks are investigated: http://www.youtube.com/watch?v=FzPYGRO9LsA